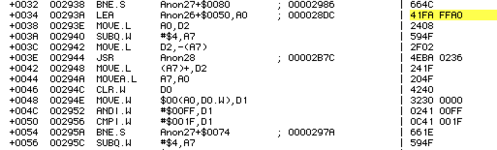
TimerInterruptFunc XREF[3]: L318.__z37___z37_PERFORM:0001124
L318.__z37___z37_PERFORM:0001125
L318.__z37___z37_PERFORM:0001126
0001132e 4e 56 00 00 link.w A6,0x0
00011332 2c 5f movea.l (SP)+,A6
00011334 10 3a 00 78 move.b (0x78,PC)=>DAT_000113ae,D0b
00011338 67 40 beq.b LAB_0001137a
0001133a 30 3a 00 68 move.w (0x68,PC)=>DAT_000113a4,D0w
0001133e 20 37 00 00 move.l (0x0,SP,D0w*0x1),D0
00011342 59 4f subq.w #0x4,SP
00011344 2f 00 move.l D0,-(SP)
LAB_00011346+2 XREF[0,1]: 00011346(c)
00011346 4e ba 00 00 jsr LAB_00011346+2
0001134a 20 1f move.l (SP)+,D0
0001134c 48 e7 40 04 movem.l { A5 D1},-(SP)
00011350 2a 78 09 04 movea.l (DAT_00000904).w,A5
00011354 42 a7 clr.l -(SP)
00011356 2f 3a 00 52 move.l (0x52,PC)=>DAT_000113aa,-(SP)
0001135a 2f 00 move.l D0,-(SP)
LAB_0001135c+2 XREF[0,1]: 0001135c(c)
0001135c 4e ba 00 00 jsr LAB_0001135c+2
00011360 20 1f move.l (SP)+,D0
00011362 6d 12 blt.b LAB_00011376
00011364 20 7a 00 3a movea.l (0x3a,PC)=>DAT_000113a0,A0
00011368 d1 c0 adda.l D0,A0
0001136a 30 10 move.w (A0),D0w
0001136c 52 40 addq.w #0x1,D0w
0001136e 66 04 bne.b LAB_00011374
00011370 30 3c ff ff move.w #-0x1,D0w
LAB_00011374 XREF[1]: 0001136e(j)
00011374 30 80 move.w D0w,(A0)
LAB_00011376 XREF[1]: 00011362(j)
00011376 4c df 20 02 movem.l (SP)+,{ D1 A5}
LAB_0001137a XREF[1]: 00011338(j)
0001137a 41 fa 00 34 lea (0x34,PC)=>TMTask,A0
0001137e 4a 78 02 8e tst.w (DAT_0000028e).w
00011382 6c 08 bge.b LAB_0001138c
00011384 70 01 moveq #0x1,D0
00011386 31 40 00 0a move.w D0w,(0xa,A0)=>DAT_000113ba
0001138a 60 06 bra.b LAB_00011392
LAB_0001138c XREF[1]: 00011382(j)
0001138c 20 3a 00 18 move.l (0x18,PC)=>DAT_000113a6,D0
00011390 a0 5a PrimeTime
LAB_00011392 XREF[1]: 0001138a(j)
00011392 4e 75 rts