cheesestraws
Well-known member
I'm confused by the structure of the .MPP driver. This is certainly the case for the one that came as far back as System 7.1, which is the earliest I've got on me.
Normally, you'd have a driver header that points to the different routines the driver provides, followed by the routines. That'd be nice and straightforward. That's not what you have here.
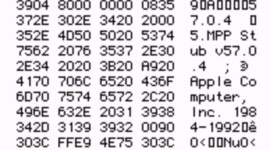
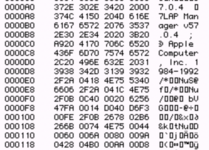
The DRVR code resource looks like it is two resources wedged into one. At the top, you have something that claims to be the ".MPP Stub":
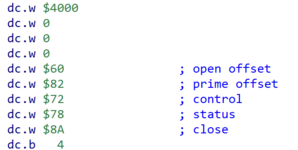
The MPP stub is a very short driver. Note that all the offsets in the header are pretty close together:
And all of these routines appear to be basically noops: Open immediately returns a negative error code, Control and Status appear to jump directly to JIOCompletion, and prime just clears a flag. Nothing complicated here.
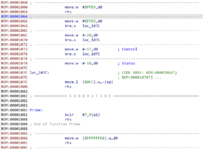
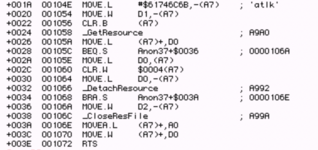
After this appears to be a load of code for the LAP Manager:
And this definitely is code, it's not just random data: there's definitely routines doing sensible things in there.
But the question is: how on earth does control get down there?
I'm going to tag @Crutch in hopes of good ideas but anyone—please—have opinions!
Normally, you'd have a driver header that points to the different routines the driver provides, followed by the routines. That'd be nice and straightforward. That's not what you have here.
The DRVR code resource looks like it is two resources wedged into one. At the top, you have something that claims to be the ".MPP Stub":
The MPP stub is a very short driver. Note that all the offsets in the header are pretty close together:
And all of these routines appear to be basically noops: Open immediately returns a negative error code, Control and Status appear to jump directly to JIOCompletion, and prime just clears a flag. Nothing complicated here.
After this appears to be a load of code for the LAP Manager:
And this definitely is code, it's not just random data: there's definitely routines doing sensible things in there.
But the question is: how on earth does control get down there?
I'm going to tag @Crutch in hopes of good ideas but anyone—please—have opinions!